
[Home] [Resume] [Work Responsibilities] [Search Page] [IT Menu]

The logon process is somewhat more complicated for a domain because logon information must pass from the local machine (on which the user is working) to the domain controller and back again. This network logon process requires the NetLogon service to establish a secure channel to a domain controller so that its accounts database can be queried.Primary Domain Controllers
In a domain environment, all nodes must authenticate logon requests with a domain controller that contains the central accounts database for the entire domain (see below). The first and central
domain controller is called the primary domain controller (PDC). It contains the main copy of the account database. Other domain controllers can be configured to make login more efficient, especially at remote sites. These secondary domain controllers are called backup domain controllers (BDCs); they contain a copy of the account database, which is synchronized with the PDCís copy on a regular basis.
As the first computer in the domain, the PDC creates the domain. Each domain can contain only one PDC. The PDC handles user requests and logon validation, and it offers all the standard Windows NT Server functionality. The PDC contains the original copy of the Security Accounts Manager (SAM), which contains all user accounts and security permissions for your domain.
In a domain environment, a password needs to be changed only onceóin the central account databaseóto be usable on any member computer of the domain. Likewise, a user needs only a single account to access resources anywhere in the domain. Only Windows NT Server machines can serve as domain controllers in a Windows NT network.
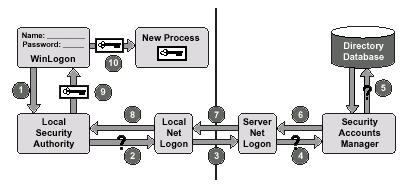
The following steps outline the domain logon procedure (illustrated below):
WinLogon sends the username and password to the Local Security Authority (LSA).
The LSA passes the request to the local NetLogon service.
The local NetLogon service sends the logon information to the NetLogon service on the domain controller.
The login process in a domain
environment. The NetLogon service on the domain controller passes the information to
the domain controllerís Security Accounts Manager (SAM). The SAM asks the domain directory database for approval of the username
and password. The SAM passes the result of the approval request to the domain controllerís
NetLogon service. The domain controllerís NetLogon service passes the result of the
approval request to the clientís NetLogon service. The clientís NetLogon service passes the result of the approval request
to the LSA. If the logon is approved, the LSA creates an access token and passes it to
the WinLogon process. WinLogon completes the logon by creating a new process for the user and
attaching the access token to the new process.
SAM SAM, Security Accounts Manager, is the Registry key that contains the entire
user and group account database. The only way to modify the data in SAM is to
use the User Manager utility (or User Manager for Domains on a Windows NT Server
domain controller). SIDís and Renaming Users The User Properties dialog box shows that although you can change a userís
full name at any time, the username is fixed. To change the username (remember,
the username is the logon name), you must choose User, Rename from the User
Manager for Domains main Window. When you rename an account, it retains all of
its other properties, including user rights and resource permissions.
Internally, Windows NT is no more fooled by the new moniker than your family
would be if you legally changed your own name. This is because Windows NT tracks
users with an internally defined Security Identifier (SID), which is like a
Social Security Number. Once itís created, an accountís SID never changes,
even if the account is renamed.